LDAP-IDP service with cidaas integration
In 2021, companies will continue to use LDAP services to authenticate users. Even when it is obvious that OpenId Connect and OAuth2 are the new de facto standard for user authentication, the change has to be well planned. Therefore, in some environments it makes sense to use migration procedures to accelerate the widespread introduction of cidaas with the help of this LDAP service. This article describes what the cidaas LDAP service does, how it can be used in companies and which security aspects have to be considered.
01
Motivation
DAP services, for example Microsoft’s Active Directory Service, Oracle Internet Directory and OpenLDAP are based on storing information in a directory tree structure. Thus, organisational structures are mapped and the employees in these organisational units are organised. The administration of a password for the employee (user) is then only a small step to enable user authentication with an LDAP service. For this reason, LDAP services are often used in companies for user authentication. Some manufacturers have expanded the directory structures to such an extent that system elements such as computers or printers are also managed in these directory services.
New and powerful standards have evolved with the advent of the Internet and the mobile era, enabling secure user authentication and more powerful authorisation management. The chart below shows the evolution of authentication and authorisation standards.
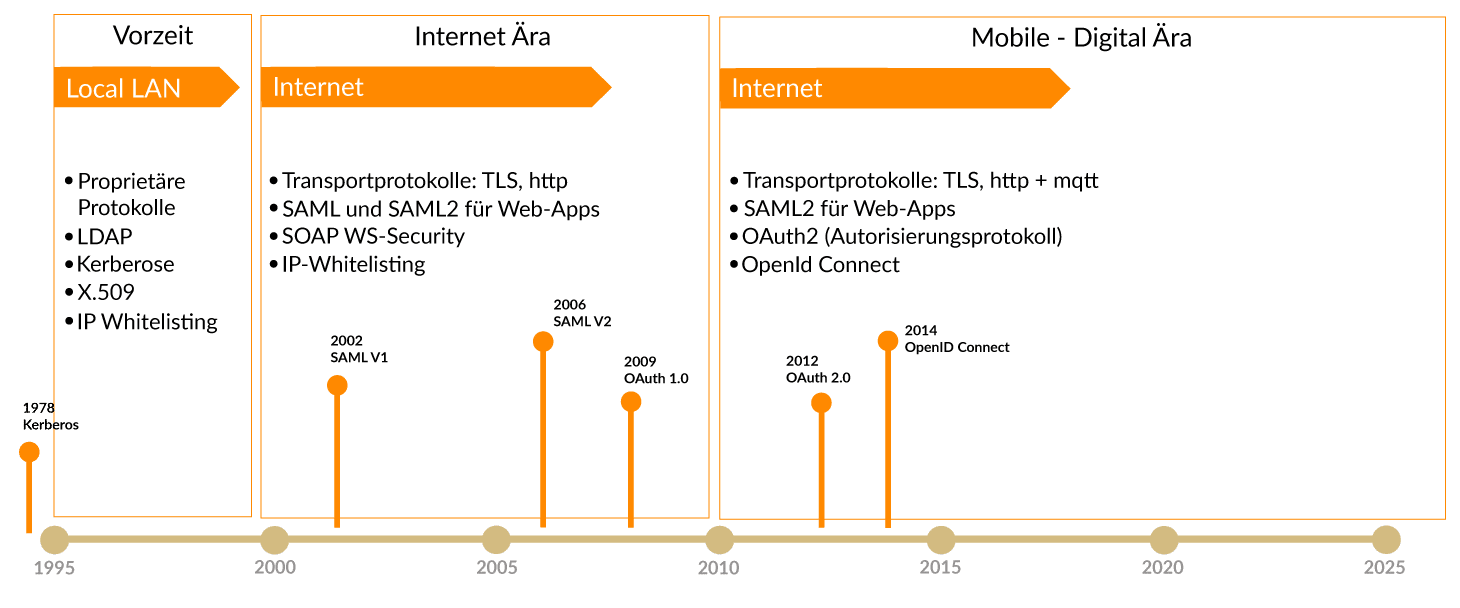
Ever since “digitalization” has become the dominant theme, secure and future proof IAM solutions, such as cidaas, have been in demand. The cidaas LDAP-IDP service is designed to enable a compatible connection of LDAP clients in order to significantly accelerate migration projects. Cidaas supports the OpenId Connect, OAuth2 and Device Authorisation protocols. In addition, cidaas offers many verification methods for users that are passwordless and in combination enable multifactor authentication.
With the cidaas LDAP service, the user authentication of an existing LDAP service in the company can be replaced, so that the user management and the user authentication are carried out centrally in cidaas. With this
- an SSO with the same user credentials is achieved
- cidaas can be used securely as a Cloud SaaS with LDAP
- users can be managed centrally (user information, locks, permissions)
- Existing applications can still be used if an OIDC/OAuth2 or SAML2 based authentication method does not or not yet work.
02
Flashback LDAP
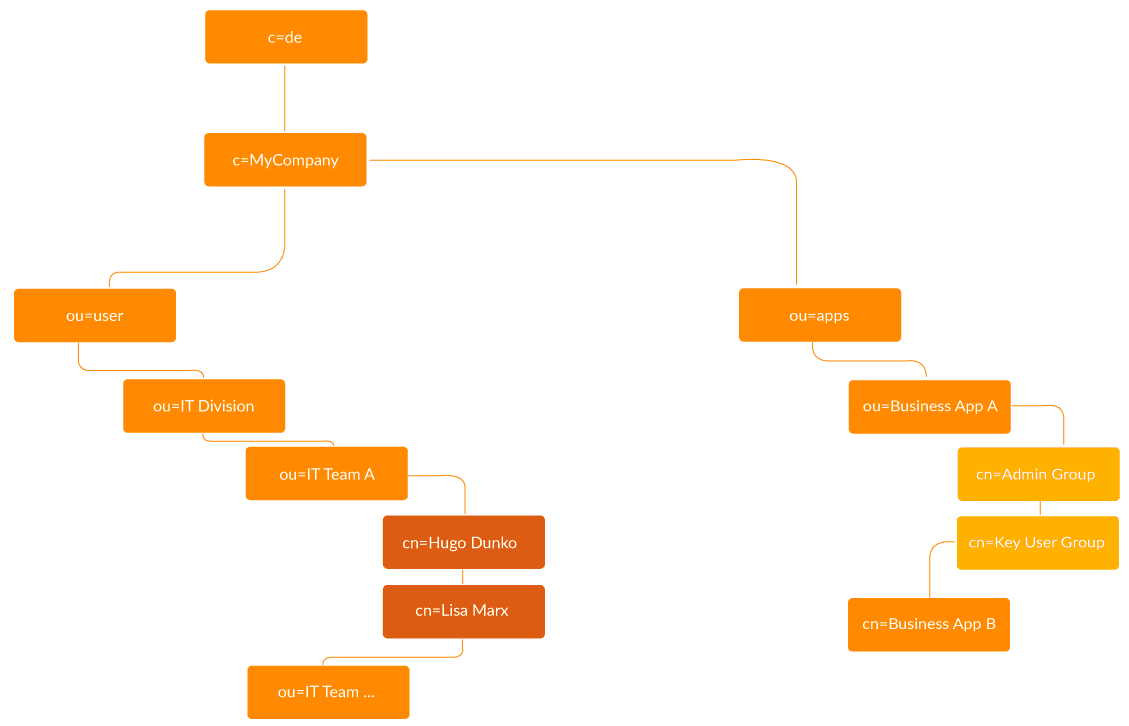
A directory tree offers the possibility to store different information and to search for this information. The idea of structuring information in a directory tree is basically good if the information follows a hierarchy. This has been a practical approach in companies for many years, especially if the organizational units are structured functionally and hierarchically. For example, to assign different permissions to applications, user groups were formed where a user group can also correspond to a user role. user groups were formed, whereby a user group can also correspond to a user role – in most systems these groups are then also mapped to roles.
For users, a password can also be managed in the LDAP element and, depending on the implementation, a history of passwords used. These passwords are usually stored as hash values (e.g., SHA-1 or SHA-256). This makes it possible to authenticate users with the combination “user ID and password” in the LDAP server.
03
Distinctions between LDAP and cidaas
It is unfair to talk about the advantages and disadvantages of both technologies or products, because the advantages clearly lie with cidaas.
03.1
Security-relevant points of critique with LDAP
- The Ldap(s) protocol does not provide for any pre-authentication of the client application, which means that basically any application can call the LDAP service.
- User authentication with LDAP can be implemented in different ways, but it is usually assumed that a search of the user has carried out first
- The administrative authentication can be considered as token authentication because the LDAP protocol is not a stateful protocol or requires a sequence of calls, e.g..
- bind with administrative user,
- search for objects or bind of a conventional user
- LDAP services must accept anonymous requests from any clients in order to provide the capabilities or structural information about the structure of the directory structure. This access must additionally be restricted, for example, by means of a firewall.
- It is basically impossible to prevent an LDAP service from returning the hashed password to the client, which makes local brute-force attacks easier.
- Fundamentally, the LDAP service is only, among other things, a “user authentication service” whose functionality is based on knowledge, namely “user ID and password”. Otherwise, the LDAP service does not offer any further verification procedures.
- As a consequence of the described weak points, an LDAP service cannot be used as a public interface on the Internet for authentication, e.g., in web applications or mobile applications.
The use of an LDAP service in a secure, closed environment is generally less problematic as long as there is appropriate monitoring and regular auditing.
03.2
Missing functions in LDAP
- LDAP services are basically structured in such a way that central administration takes place; shared administration causes a high organizational effort. The management of sub-trees is a theoretical construct that rarely works in practice because, for example, users in several organizational units have to be managed from a central location.
- User self-services are difficult to achieve via the LDAP protocol and are usually implemented via additional products.
- The link between user authorisations and an application cannot be verified by the LDAP service because only the data is available but not the necessary logic.
- Multi-factor authentication or fraud detection is not available in LDAP services.
03.3
Other paradigms
LDAP implements a directory tree, cidaas does not. This means that navigation within hierarchies is not possible in a meaningful way in cidaas. Instead of a tree structure, cidaas uses a group concept and user roles that can be used flatly and simply from an authorization perspective. This results in more powerful ways to filter users.
Cidaas implements only “group” and “user” objects.
03.4
Reasons for using the cidaas LDAP Service
The use of the cidaas LDAP Service is possible with the implementation of cidaas. It is useful if existing applications need LDAP for a defined period of time and will only use new authentication standards in the context of their lifecycle management.
04
Integration of cidaas LDAP Services
04.1
Integration architecture
The cidaas LDAP service is provided as a Docker image and operated on a server system in the company. The LDAP service should not be operated in the cloud, nor should it be publicly accessible.
cidaas can be used as SaaS, as intended, as the LDAP service is connected via secure, internet-enabled protocols.
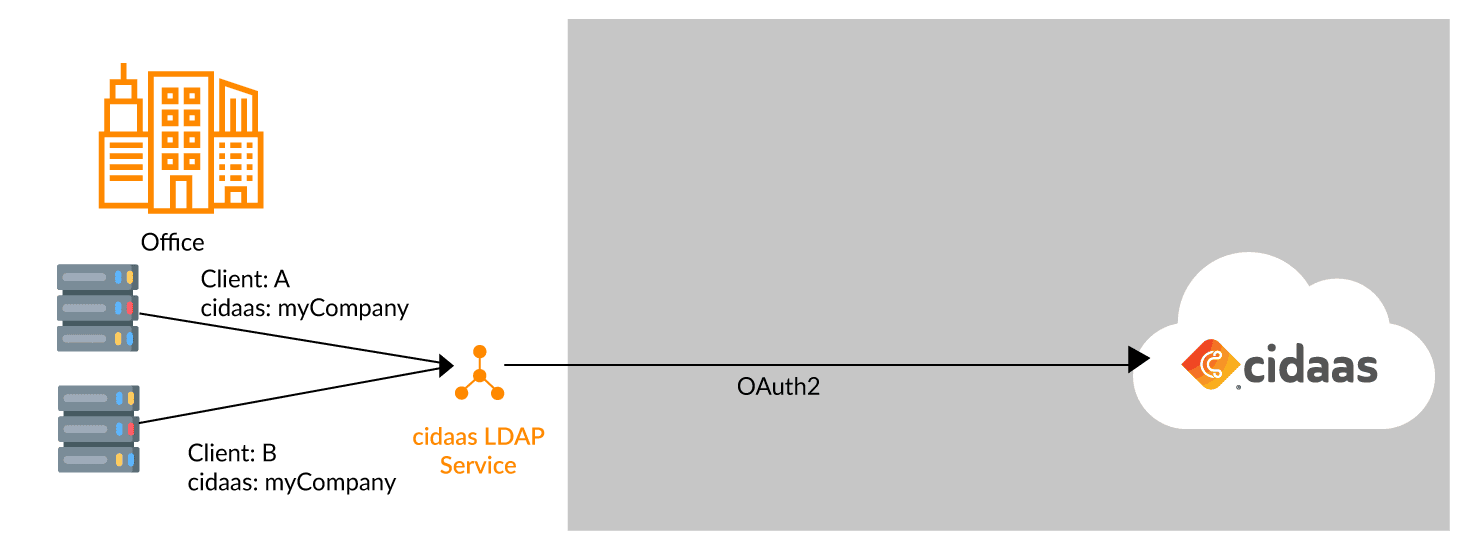
Each LDAP client is configured in cidaas as a standalone app and assigned individual group and role permissions. This ensures that a client system does not gain access to user information that is not in their scope. The cidaas LDAP service can therefore be considered more secure than traditional LDAP services.
04.2
Restrictions
The cidaas LDAP service has a defined functionality that is limited to user authentication and authorisation only.
- Editing the entities in the LDAP directory through the service is not possible and not desired. Such configurations are to be made in cidaas, via the admin dashboard or the cidaas APIs.
- The cidaas LDAP service does not provide MFA functionality. If MFA is required, it is recommended to replace LDAP in the client and use SAML2 or OpenId Connect.
- The cidaas LDAP service offers entity search for the object’s “user” and “group”.
- No cidaas LDAP schemes can be retrieved, a generic scheme is supported.
05
Suggestions: Replacing LDAP Services
In the enterprise, the replacement of LDAP services should be considered for several reasons:
-
- As such, due to the weak authentication solution,
- Due to the lack of integration possibilities with cloud software solutions,
- Aufgrund der suboptimalen Verwendung in Umgebungen, in denen Work-From-Home oder mobiles Arbeiten realisiert wird – da in diesen Fällen stets VPN Netzwerke notwendig sind und
- Because of the suboptimal use in environments where work-from-home or mobile working is realised – as VPN networks are always necessary in these cases, and
because other possible uses of LDAP, e.g., device management or domain administration, have long since been taken over by more powerful device management solutions.
The use of cidaas replaces LDAP-based authentication. However, the cidaas LDAP service is suitable as a quick win so that systems can continue to be used in compatibility mode.
