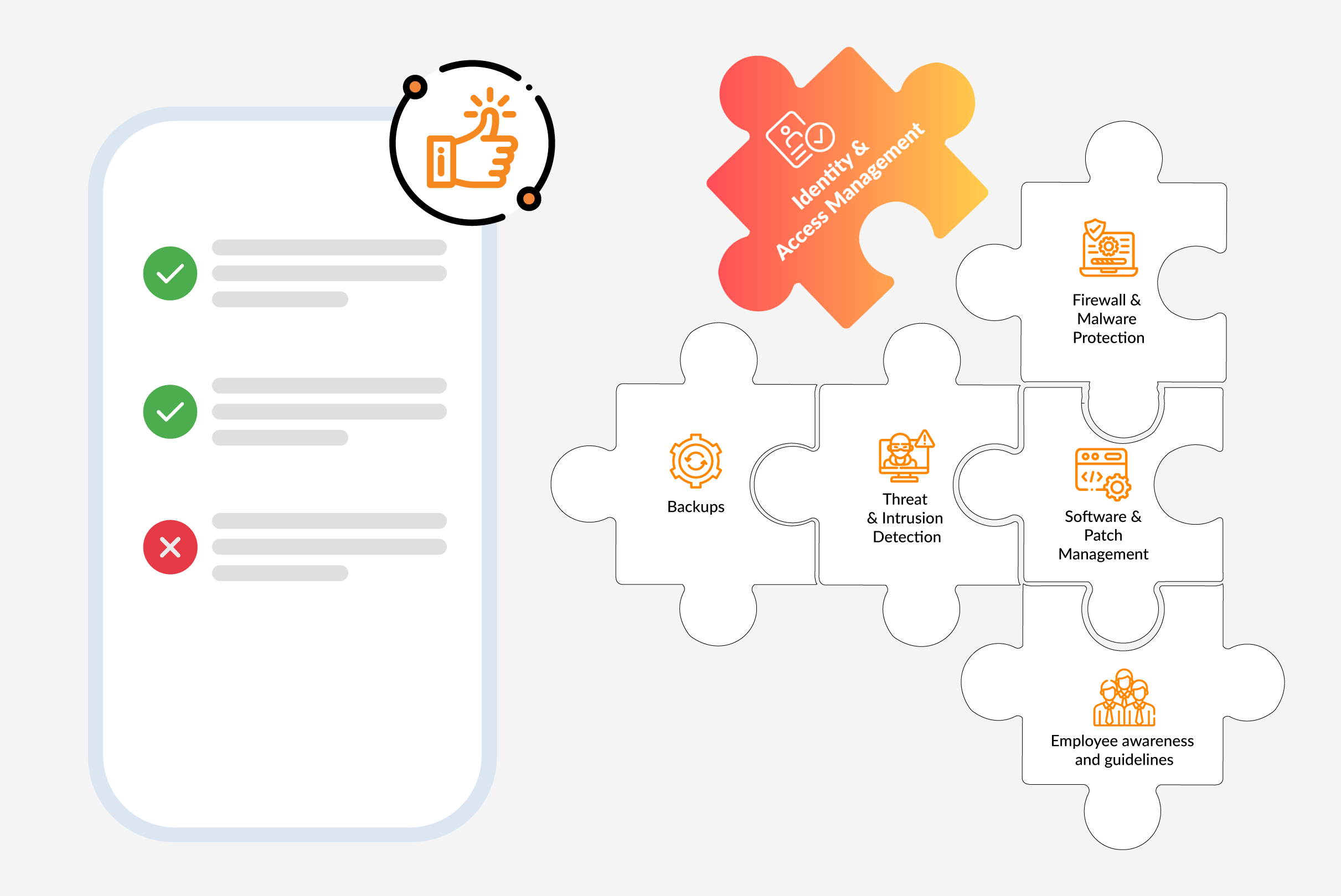
Identity & Access Management as a Core Building Block of Cyber Insurance: Authorization Management
In our second blog in the series, we take a look at authorization management and how businesses can use it not only to meet cyber insurance requirements, but also to establish an end-to-end authorization concept.
Authorization management or also known as access management
Authorization management, or also known as access management, ensures that the right people have the appropriate access rights to business resources. In this context, the management of authorizations, i.e., assigning, changing, or revoking authorizations on the one hand, but also the continuous checking of users’ authorizations so that users do not have too many authorizations on the other hand, is important. Users are not only employees, but also suppliers and partners or in the area of Customer Identity & Access Management, customers (B2B and B2C). By implementing effective authorization management, organizations can control who has access to which systems and data, thereby minimizing the risk of unauthorized access and potential data breaches.
Authorization is an essential functional component of the cidaas platform, and any authorization concepts can be implemented based on the extensive group and role management of cidaas. On the one hand, the authorization is enforced directly in cidaas, for example, access to applications via group and role restrictions can be configured directly in cidaas. On the other hand, a user’s group and role information is also transferred to the integrated application, so that it can implement further authorization based on this.
Why do cyber insurance companies require authorization management
Cyber insurance companies often require businesses to establish a comprehensive authorization management system as part of the insurance policy terms and conditions. The reason for this is that end-to-end authorization management significantly reduces the risk of unauthorized access and thus also the risk of a successful cyber-attack.
The benefits of authorization management for businesses and the cyber insurance:
- Risk reduction: Effective authorization management enables enterprises to control access to sensitive data and systems. This minimizes the risk of unauthorized access, data leaks, or cyber-attacks that could lead to insurance claims.
- Preventive measures: Comprehensive authorization management makes it possible to restrict access to certain functions or information on a “need-to-know” basis. This reduces the possibility of employees accidentally or willfully causing damage.
- Compliance: Businesses often have to comply with various regulatory requirements and data protection laws. Authorization management can help meet these requirements and prevent violations, which in turn increases the chances of a successful claim settlement in the event of an insurance claim.
- Real-time monitoring: An authorization management system enables continuous monitoring of user access rights and activities. This allows suspicious activities to be detected at an early stage and appropriate countermeasures to be taken to limit potential damage.
- Improved incident response: In the event of a security incident, a well-documented authorization management system helps identify the scope of the security breach and potential vulnerabilities. This information is invaluable to response teams as they can more effectively contain the incident and minimize the damage.
A solid authorization management system not only meets the requirement of cyber insurance, but also strengthens an organization’s overall IT security. It reduces the likelihood of successful attacks, protects against insider threats, ensures compliance requirements are met, and enables more effective incident response. Therefore, authorization management is not just a cyber insurance requirement, but should be an essential component of your IT security strategy.
On our landing page – Identity & Access Management for Cyber Insurances – you can learn more about how cidaas can help with the implementation of cyber insurance requirements.
Read also the other parts of our Blog series “Identity & Access Management as a core building block of cyber insurance”:
- Identity & Access Management as a core building block of cyber insurance: multi-factor-authentication
- Identity & Access Management as a core building block of cyber insurance: Detecting cyber attacks
- Identity & Access Management as a core building block of cyber insurance: reporting and recertification
