
App Developer Portal: The best person to manage an Identity & Access Management System
- It enables the creation of a consistent identity across all communication channels.
- It provides a seamless Single Sign-On experience.
- It increases access security by implementing multi-factor authentication.
- It provides user-friendly authentication and login experience.
But who is the best person to manage Identity & Access Management? Who makes the decisions about who gets access to a specific application? Who decides whether multi-factor authentication is required for a service? And who designs the user registration and onboarding process? Do you need a dedicated IAM team for this, or is the IT department best suited, or should perhaps the business units make these decisions?
As you can see, many questions arise which we would like to discuss in more detail in this article.
Who is interested in changing settings in cidaas Identity & Access Management systems themselves?
Before we can answer the above questions, we must ask ourselves who is interested in changing settings in the first place.
Overall, the interests between a company (enterprise) and Customer Identity Management show some minor differences.
There is no question that departments have a vested interest in implementing the processes they deem appropriate for the user. This often varies greatly depending on the function of the system, whether it is to attract potential customers or to perform important, sensitive tasks such as banking transactions.
The main objectives are:
- Creating an impressive user experience.
- Recognition across all channels (brand image).
- Simplifying the use of services.
- Ensuring valid user accounts through secure identity verification and avoiding service fraud.
The technical teams implement the requirements of the business units and provide new functions in their applications, regardless of whether they are web or mobile apps.
The story outlined here is highly simplified. In a company, many teams can develop different services.
Who is actually allowed to change settings in cidaas Identity & Access Management systems?
The saying “many cooks spoil the broth” also applies in part to the settings of an Identity & Access Management System.
However, many “cooks”, especially those with specialized knowledge, can make the configuration more efficient. A “cook” who understands what his “dish” is for and what requirements must be met can contribute significantly to the configuration of his application.
That’s why we developed the App Developer Portal. Here, each team can manage its own applications. This way, the number of “cooks” is reduced, and the right teams can make the settings.
However, there are some proven requirements that should be taken into account:
- The developer should have an understanding of OAuth2 and OIDC, especially security related settings. Scopes should be carefully selected.
- Conventions should be adhered to. Correct naming is crucial so that others know what application is behind it.
- Some settings should be centralized, such as provider approval, permission for disposable email addresses, available verification methods, and display of profile fields.
The Developer Portal enables decentralized management for efficient operation, quick configuration, and independent work of the teams – who is the best person to manage an Identity & Access Management?
With the Developer Portal of cidaas, teams can create, update, and customize their apps (OAuth2 clients) independently. If there is a need for workflow changes, new mandatory profile fields or multi-factor settings, teams can act independently and make configurations quickly.
In addition, the portal offers dedicated evaluations of the applications, such as the number of daily logins and new registrations via the service. Besides the apps for users, integrations can also be made with other systems, so-called “non-interactive clients”, to ensure internal communication via OAuth2 and to perform specific actions.
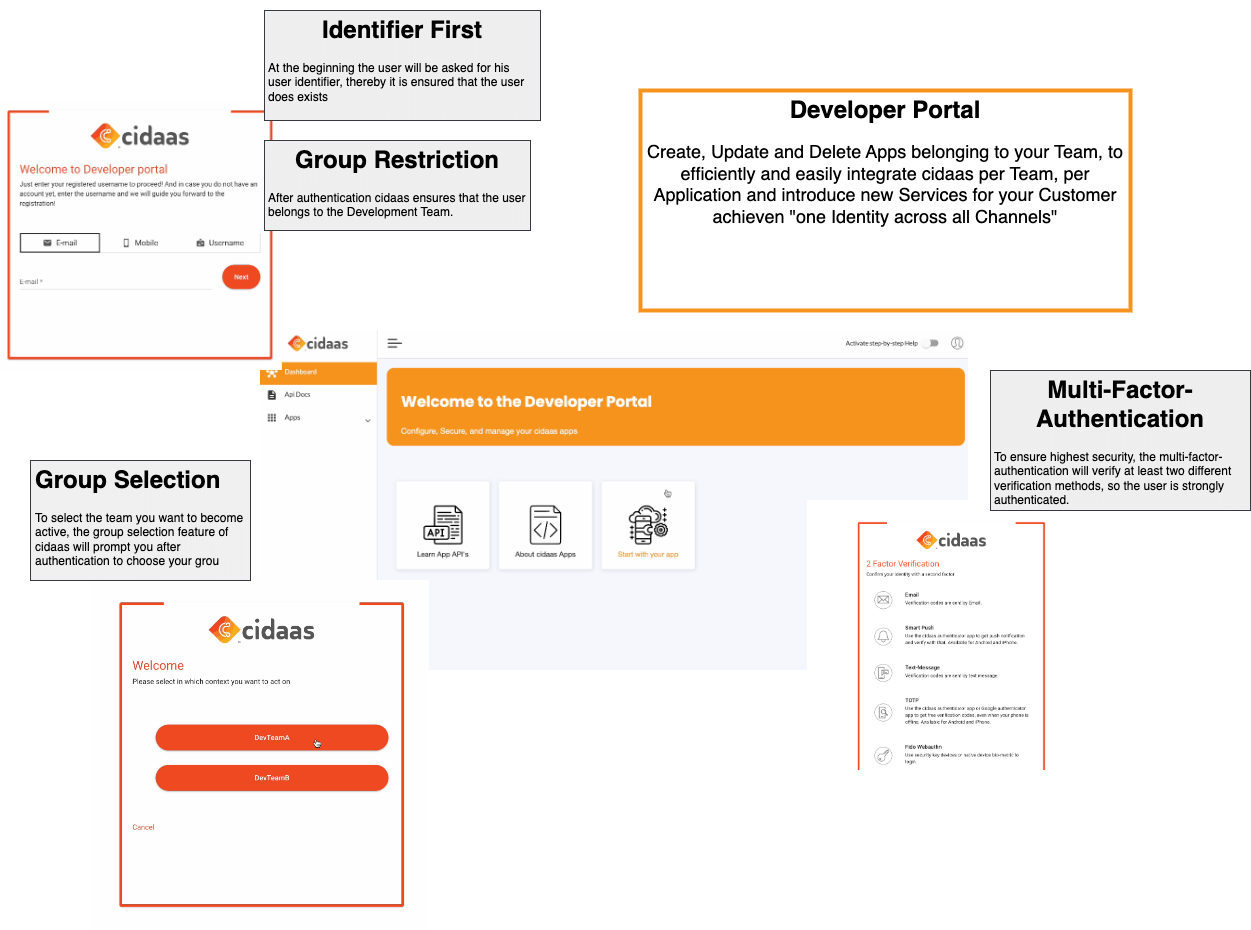
| Function | Description |
|---|---|
| Group / Role Restriction (Validation) | Based on the Group Role restriction feature, only people who belong to the Developer group are allowed to log in to the Developer Portal. |
| Group Selection | As soon as a developer logs in, he is asked, for which team he will be active in the next step. This is done via Group Selection if he is a member of several teams (DeverloperGT groups). |
| Multi-factor authentication | App configurations are highly sensitive, so multi-factor authentication is mandatory. |
As already mentioned, the representation sketched here is a highly simplified version. In order to provide you with a comprehensive insight into cidaas to present the diverse possibilities of cidaas’ leading European solution, or the cidaas App Developer Portal we would be happy to get in touch with you and arrange a demo presentation.
