PSD2 – Universal login using OpenId / SSO for web interfaces: Digitalization ensures market share

With the PSD2 beginning 2018, banks are obliged to secure their new web interfaces. The “how” is associated with precisely defined requirements. Thomas Widmann (CEO WidasConcepts) talks about the various possibilities. The cleverest though should be a universal login.
from Thomas Widmann, WidasConcepts
With PSD2 many other third-party providers become the Payment Service Providers (PSP) and / or Account Information Service Providers (AISP). The objective of the PSD2 standard is to give a new impetus to electronic payment and to adapt it to modern requirements in the wake of digitalization. For example, services and their payments can be linked more easily. Instead of or to complete the payment by credit card, paydirect, immediate transfer or Paypal in online shops, the PSP offers the direct payment option directly in the service-flow, say for micro-payments or subscription payments. What is clear is that with this, the paperwork, the invoice, also disappears.
In order to create transparency in these payment transactions, it is necessary for an AISP – and of course even for all financial institutions that the customer uses. The overall financial status of a customer is therefore no longer anchored in a single bank. AISPs are expected to offer the overall financial status and other services free of charge in order to generate revenue over add-on offers and commissions. As of now, for AISPs, it is all about the perfect user experience.

Strong User authentication
Banks have long used user authentication (login) and legitimacy check (transaction-related authorization with TANs) to identify customers. Especially with legitimization, new methods of two-factor authentication are being developed, which should increase security. These include photo-TAN, TAN generator devices, SMS-based TAN and now also apps that provide TANs. The idea of making these already implemented procedures usable, also in the course of PSD2 seems to be obvious from the banks’ point of view.
As a matter of fact, this assumption is valid only at first sight, because:
-
- The customer authentication (login) at a bank is a rather weak authentication. For example, if the account number and PIN are used by several people. In this case, the information is stored “unsecure” for easy access on relevant portals and apps.
- The constant need to check for legitimacy of TAN for each individual transaction and, for example, also micro-payments has long since been overtaken because it does not correspond to the requirements of the customers in terms of ergonomics and handling. That it works differently is proven by Paypal for e.g.; an extremely successful payment platform shows that it is different.
- Both AISPs and PSPs will help ensure that the strong customer authentication becomes the standard – ergonomics and handling being the decisive factors here. One of these standards today is OAuth2, whose success is based on the fact that:
a. User credentials remain hidden for third parties
b. A concept for the login refresh is given and users can stay long online – constant logging on and off is a thing of the past.
c. OAuth2 has established itself as the de facto standard for securing web interfaces.
d. Tech giants such as Facebook, Google, Amazon, Salesforce or Microsoft, have since long used these processes successfully, and thousands of companies are following this concept.
There is a general consensus that two-factor authentication is to be applied when it comes to user identification if there are uncertainties about the identity of the user.
- Two-factor methods are constantly changing. There still are banks who believe that the different procedures have become a favorite among their customers. Nevertheless, the methods are subject to continual development. With mobile devices, the introduction of biometric methods and the Internet of Things (IoT), the changes will further only continue to increase. At the same time, alternatives to authentication are possible, where the EU can contribute to reliable identification with the eID.
The secure and unambiguous customer identification thus becomes the key to success in the competition. In any case, it is high time than ever for a bank to think about whether or not to in fact take up on themselves the development of a strong customer authentication and management of customer identities and moreover if they can afford it. Ultimately, such a solution must meet numerous requirements to be competitive.
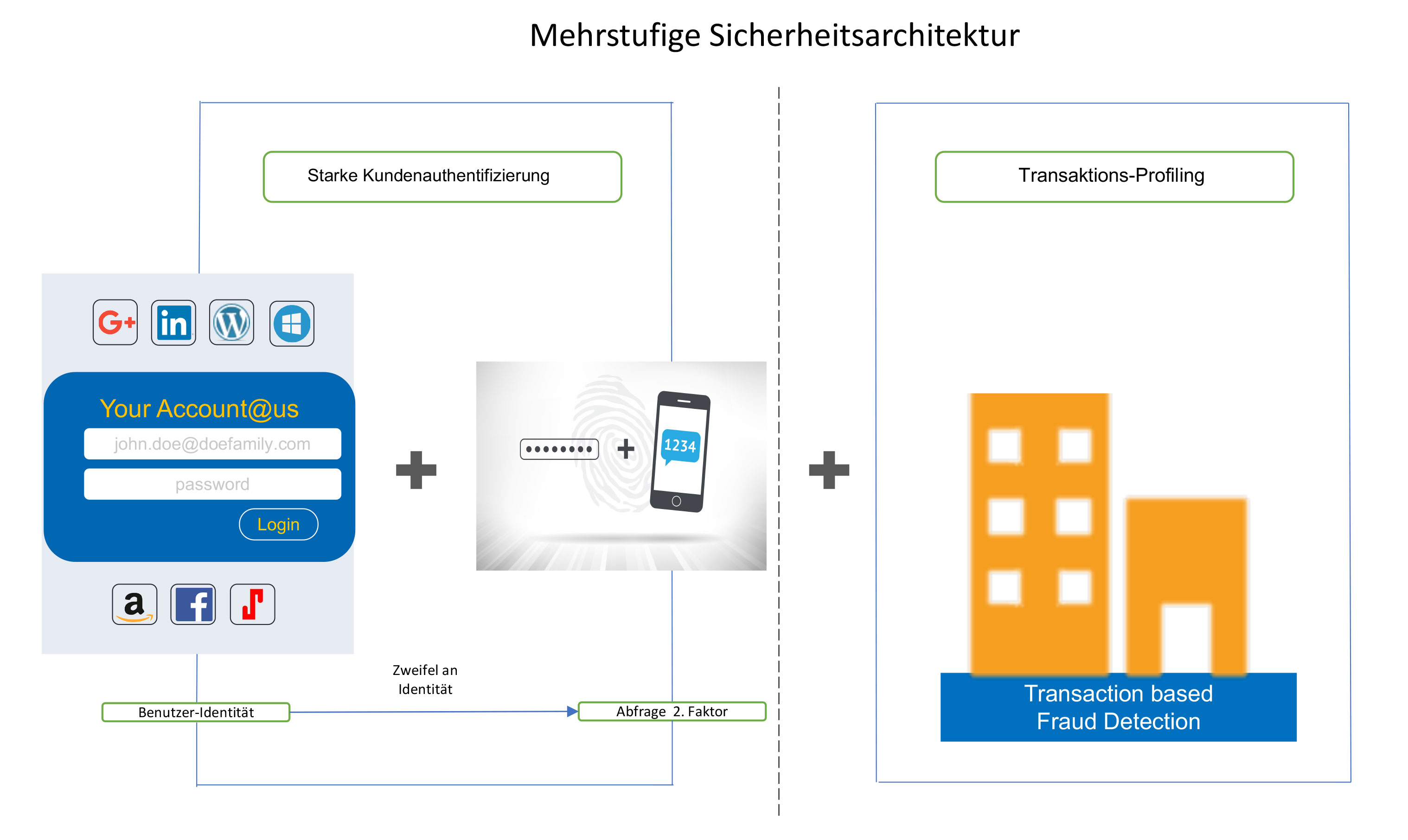
Fraud detection
In order to reliably prevent fraud, a multi-level security architecture is required:
1. The user identity is securely determined.
2. In the event of uncertainty in the user identity, the identity of the person is controlled by another factor, for example by biometric procedures.
3. Lastly, in the case of a bank, the persons and accounts should be subjected to profiling in order to detect inconsistencies in the customer’s transaction behavior. (Figure 1)
Requirements
With digitalization, processes and systems are changing, which is why new requirements are emerging for user authentication and authorization. This includes technical and IT requirements:
- Technical requirements
- Securing web interfaces (APIs) with OAuth2
- Option to have Single Sign On (SSO), especially important in the case of Single Page Applications.
- Use as Universal login across all channels
- Banks own iOS and Android Apps
- Portals
- Third party apps and portals
- Registration and login by prospective customers in sales processes
- 2 factor authentication
- One time passwords
- User profile
- User self services (changing passwords, reset, user profile edit, choose the 2 factor authentication method, manage devices)
- Integration of social logins and other login providers
- Tracking of customer behavior across all channels – Know your customer
- Outstanding User-Experience during registration and login
- Checking of addresses during user registration
- IT Requirements
- Simple/easy integration of security in Apps and web services through the use of software development kits (SDKs)
- Configurable security settings
- User admininstation user interface and interfaces
- Administration and Monitoring of all systems and channels
These requirements are now standard among many Internet companies. In addition to the technical requirements, there are also new aspects on the agenda of a bank: this includes user authentication for prospective customers and know your customer. The latter is the only way to address users in a personalized way.
Icing on the cake: to become an OpenId-Provider
If you want to secure long-term market share, you should not only care for your existing customers, but also deal intensively with prospective customers. The possibility to identify potential customers through their login opens up this circle of interested parties: Credit institutions, which enable users to log in to other companies, not only simplify new customer acquisition, but also opens up a wide range of services and offers, the management of which you hold in your own hands.
Many ID providers are still insignificant today. A company that actively uses Customer Identity Management and wants to become a successful OpenId provider must choose the most important OpenId providers for its business. Only so is it possible to reach a large number of people in the target group. At the same time, the presentation of more than four OpenId providers proves to be rather confusing for the users. Social-login providers are currently most successful, especially Facebook and Google. The reasons for this are understandable: Social login providers offer the identity of the user, which usually includes strong authentication, addresses, his interests, professional experience, employer, hobbies and even access to the user’s contacts. In addition, they can also share activities on the social media platform, such as ratings, comments, and recommendations. The questionnaire at the end of the text summarizes the key points a bank should work out when it wants to become an OpenId provider.
Technical implementation possibilities
A user authentication can be implemented by a bank in at least three ways. For example, it is possible to use a stand-alone development using some OpenSource frameworks. Alternatively, the development and adaptation can be used on the basis of an existing authentication and authorization service (for example, Keycloak). Finally, a professional customer identity management system can also be used (eg cidaas, janrain, gigya, auth0).
Development and adaptation based on existing services
If a bank implements a virtualization platform in the wake of PSD2, as part of the Platform as a service implementations for the management of user accounts and authentication are required. Examples for this are CloudFoundry (UserAccount and Authentication (UAA) servers) and also OpenShift (SSO Server (Keycloak)). These services offer a functional scope that is quite consistent in itself. The main focus is on the security and OAuth2 flows, whereby two-factor authentication is also party possible. As with any packaging of a platform, these services technically complete these virtualization platforms.
For an adequate customer identity management, further steps and functions are necessary, which must be added further during the development:
1. Reliable end-device detection
2. Location-based recording during registration, login
3. Performing Address Checks at the time of Customer Registration
4. Management of login / registration UIs
5. Continuous profiling of user actions to propose two-factor authentication and get to Know your customer
6. Option to add events depending on the user behavior: Business software then applies Know Your Customer, e.g. to respond individually to particularly active users or users who have not used a channel for a long time
7. Two-factor authentication must be newly added as per needs, such as bio-metric procedures
8. Additional customizations, e.g. Custom Login Provider or Communication Templates for User Self Services
The development and adaptation effort for the use at a bank is therefore considerable. Virtualization platforms are equipped with SSO services, which are required to secure platform administration. However, only the security and OAuth2 management part of a Customer Identity Management is covered. However, if you want to become a serious competitor, you have to measure up with solutions such as those offered by Google, Facebook, Linkedin or Amazon on their portals and apps.
Use of professional customer identity management systems
A professional customer identity management provides nearly all the functions necessary for secure and reliable user identification. In addition, dashboards and reports provide very good overview into user behavior. The advantages from the point of view of a credit institution are obvious:
1. In real-time, the business software is made aware of different events and can thus address users (customers) correspondingly.
2. Various two-factor methods are selectable, in tune with the personal needs and the environment of the user
3. Standards such as OAuth2 and OpenId Connect enable the bank to act as an OpenId provider, should it be useful from a business policy perspective
4. User profiles, user self-services included
5. Multiple identities can be linked, such as Google with LinkedIn and the bank’s user account
6. Numerous SDKs and convenient admin dashboard allow for an easy integration of customer identity solutions into the bank IT
7. The application extends to/ranges in various professional customer identity management products from the virtual online world to the real world (offline) in the branch or to the intelligent device, which is used in the self-service environment.
There are many reasons that stand for a professional Customer Identity Management, and very few against. One challenge is, for example, to process customer data according to EU law. This requirement is not met by all solutions. There are, however, providers who are abide by the EU law per se, or which follow the ordinances and thereby fulfill this requirement.
Data security is honored by the customer!
Banks, which can uniquely identify customers and prospective customers on all portals and apps through a one-time login, are able to securely track their activities and create an outstanding user experience. With PSD2, additional access channels are created to the bank where users are constantly connected to the bank. With strong, reliable authentication, TAN-based legitimation audits will soon be a thing of the past because, in conjunction with downstream fraud detection systems, customer behavior is well validated and fraud has no chance. Recognizing customers also means leveraging collected insights into sales and service in order to delight customers through a hyper-personalized, and thus unique, user experience.
Is the OpenID provider model suitable for your bank at all? The questionnaire:
| Question | Description | Fulfilled |
|---|---|---|
| High user base present? | Here we speak of millions of users who would like to address a shop with this login. | |
| Does the company receive all relevant information from the customer? | If this is only about the identity and address data, this is probably not enough for many. The ace that one would like to draw is the customer’s credit rating.
Does the bank actually have the full view of the finances? |
|
| What possibilities does the bank offer to share the user information with other customers in the bank? | Now, banks are not known to offer a social platform for communication between their customers. This is very rare.
However, for a company that looks for an OpenID provider, it is definetely a significant plus when the customer shares his experience in networks. |
|
| Is an excellent user experience for registration and especially login and 2 FA given? | If the login is too unhandy, e.g. Due to the UserId and password guidelines, then customers will not use this social login. | |
| Would the bank offer other OpenId providers for their own customers? | Then it almost closes the option for the bank to be an OpenId Provider. OpenId only works with a bank’s own customer identity and credentials.
This also excludes the possibility for a bank to take advantage of several OpenId providers. |
|
| A company is spoiled for choice in choosing the social identity provider. So why use the bank? Does the bank see itself among the first 4 OpenId Providers? | Facebook, Microsoft, Google, Amazon, Linkedin are very popular. Perhaps a very large AISP is much more suitable to be an OpenId Provider – it has the entire financial status of the customer at least. |
If a question is answered with “not fulfilled”, then it is good to refrain from the OpenId provider model.
