
Success Factors for Software as a Service (SaaS) Provider – Customer Identity & Access Management with Group Management and Integration of Identity Providers (IdPs)
With the increasing demand for Software as a Service, the requirements for Customer Identity & Access Management are also growing.
In this blog, we will focus on the features that a modern Customer Identity & Access Management must-have in a B2B context. These include comprehensive Group Management and the integration of Identity Providers (IdPs).
Group Management – the Must-Have in B2B Customer Identity & Access Management
While the separation of the user base for different customers was achieved in classic software products with on-premises operation simply through the technically separate environments, multi-tenancy approaches are often used in Software as a Service.
With multi-tenancy, customers’ individual environments are no longer deployed as a separate software solution; instead, one software solution serves multiple customers. In this context, each customer or environment of the customer is called a client or tenant. The tenants are usually separated logically and no longer technically.
Due to the multi-tenancy approach, more extensive identity management is now required, which is able to manage the users of the individual tenants, and also establish a uniform identity across all tenants. This is where group management comes into play – with modern group management, the individual customers or tenants can be represented as a group in which the users are members. For better illustration, we have sketched an example.
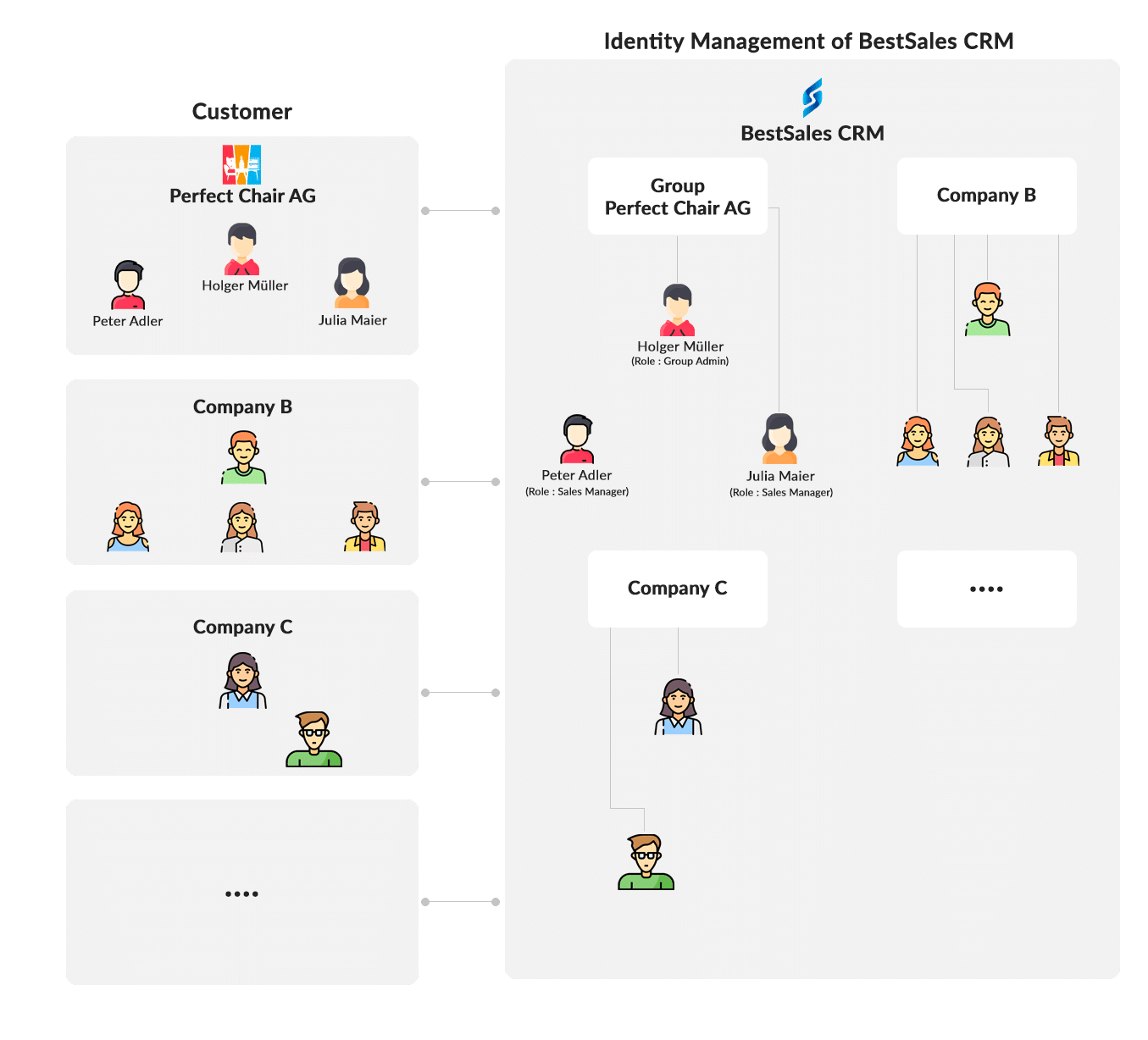
- “BestSales CRM” is a cloud CRM that is offered as SaaS.
- “PerfectChair Inc” is a manufacturer of chairs and uses as CRM – “BestSales CRM”
- “Holger Müller” is the head of sales at “PerfectChair Inc” and has registered via a Self Service Sign Up Process and purchased 3 user licenses for the “BestSales CRM”.
- “Peter Adler” is a sales representative in Mr. Müller’s team
- “Julia Maier” is also a sales representative in Mr. Müller’s team
As can be clearly seen in the diagram, the group management allows the customer’s corporate structure to be mapped in the Customer Identity & Access Management of the SaaS provider.
The cidaas group management offers a comprehensive set of functions. Groups in cidaas can be hierarchically structured and categorized by individual group types, thus the mapping of more complex use cases and company structures is easily possible. As a small example a company with different locations could have a parent group of type “Company” and different subgroups of type “Location”. The cidaas group management also enables self-administration, through which a group administrator can manage the members of his own group, i.e., assign or remove roles and rights, invite new users or remove old ones. More about cidaas group management
Grouping the users of a tenant creates a logical separation of the users and the assignment to an instance. However, users are still unambiguous about the entire Customer Identity & Access Management. This results in different scenarios.
- The users of a customer can be easily added to other environments/tenants of the customer. This is often the case when a customer has one or more test environments in addition to a production environment.
- The partners of the SaaS provider often serve multiple customers, and thus the assignment of a partner’s users to multiple tenants makes sense here as well.
In both scenarios, the benefits of having a unique identity across all tenants are obvious. The user comfort for the user of the customer or the partner is significantly higher. One account and one login – the user can select the tenant himself after successful login. Different accounts, with different access data, mostly with different login URLs, cause frustration for users. Frequent password forgetting processes and insecure access are the result.
Group management creates another important basis – the logical separation makes it possible to offer customers self-administration of their own users. For example, a group administrator can manage the roles and rights of users or add or remove users. To take up the example from above, Mr. Müller as “Head of Sales” and in his role as “Group Admin” – can invite Peter Adler to the “PerfectChair Inc” tenant and give him the role of Sales Manager. Self-administration is very important for numerous reasons:
- The administrative effort for the SaaS provider is reduced because he no longer has to actively take care of user management, but delegates this to the customer.
- Customers are able to quickly get started with the SaaS services and invite other colleagues. This is not only a convenience factor but also creates trust. Customers prefer to be in control of their own instances.
- For customers, self-administration brings a massive speed advantage – no waiting for SaaS support – so “Peter Adler” can start selling faster 😉
Customer IdPs – easy integration, big impact
Complementary to group management, there is another feature that can be easily used, and has a great effect – the integration of Identity Providers (IdPs). The identity provider functionality is already widespread due to the so-called social logins. For social login, for example, Facebook or Google are the identity providers. In the context of SaaS providers and B2B customers, however, the focus is shifting from social logins to the customers’ identity providers. Today, more and more companies use Identity & Access Management, which they would like to integrate within the best case – all or at least with as many applications as possible that are used in the company, thus also with the SaaS solutions that are used.
To take up our example from above – “PerfectChair Inc” uses Identity & Access Management and would like to integrate this with “BestSales CRM” in order to control users and access to the CRM uniformly.
The integration of Identity Providers (IdPs) into a modern Customer Identity & Access Management, like cidaas, is easy to implement and runs over the standard OpenID Connect, OAuth2 or SAML 2.0. It is also best to offer the configuration of the IdP in self-administration to a group administrator in order to reduce the administrative effort on the part of the SaaS provider here, as well as to increase speed and flexibility for the customer. An integration of different IdP buttons into the user interface, as known from social logins, is not possible. On the one hand, the login UI is overloaded with additional buttons for many customers, on the other hand, the SaaS provider does not want to reveal the customers and the preferred authentication of the customers directly.
The integration of the IdP into the login process can therefore only be done in two different ways:
- With an identifier first approach, where a user first enters the email and if an IdP is configured for that user, it is then forwarded to the customer’s IdP.
- Via a separate (sub-)domain, which each customer receives and where the IdP is directly integrated into the login process.
Back to the example: “PerfectChair Inc” sets up the OpenID Connect configuration for the SaaS solution “BestSales CRM” in its own Identity & Access Management and configures the OpenID Connect parameters (such as ClientID, Client Secret and Well-Known URL) in “BestSales CRM”. In the login process, a separate domain for “PerfectChair Inc” could now be used as described above, e.g., perfectchair.bestsalescrm.com, where users either see an IdP button or are even redirected directly to the IdP of “PerfectChair Inc”; or via an Identifier First approach as shown in the following diagram.
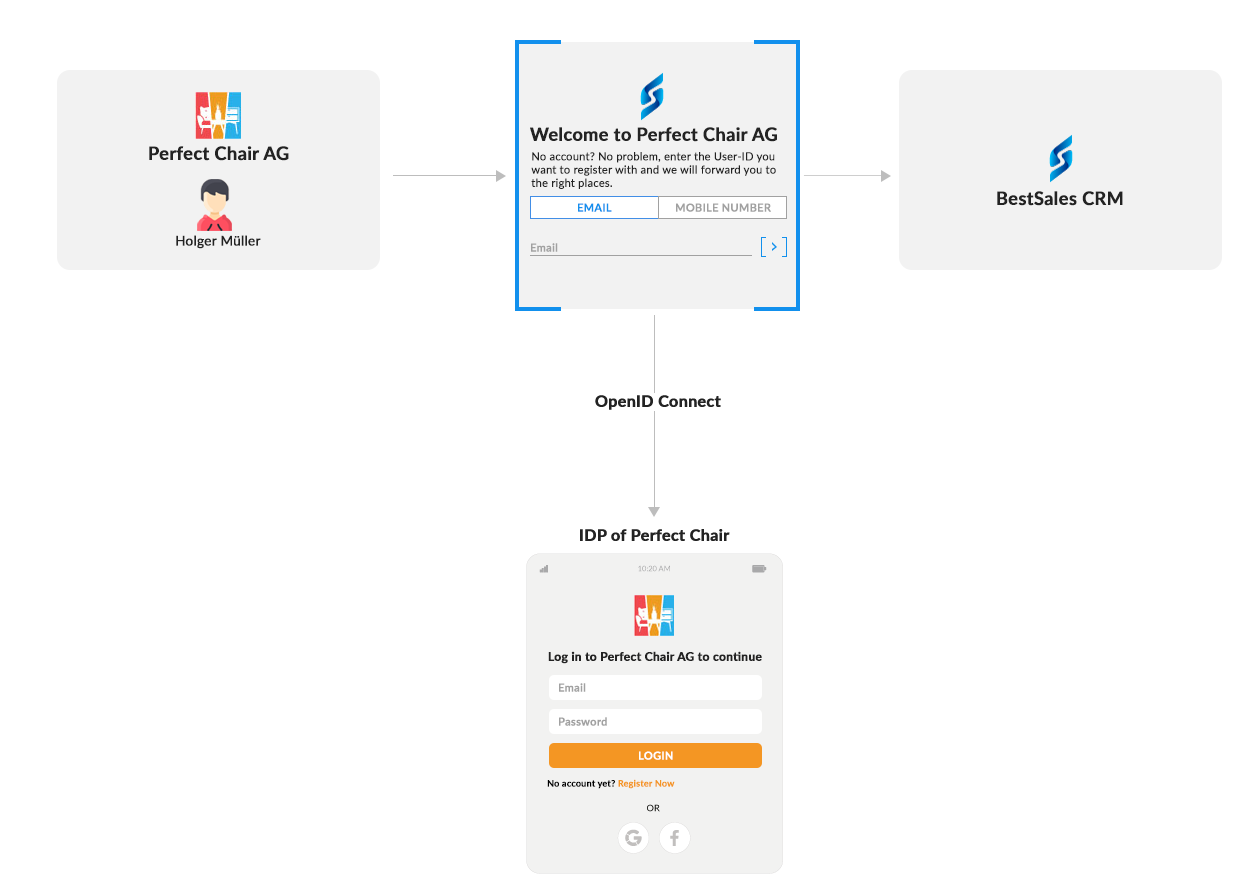
Whether separate domain or identifier first approach depends on different factors. On the one hand, the architecture of the Software as a Service solution plays a role; if customers are already provided with separate domains, the second option is only logical. If the start is the same for all customers, option 1 may be the better choice. User comfort, customer focus and other factors also play a role in the decision. Finally, it is important that the integration of IdPs is made possible because many companies require integration with the IdP, and no collaboration should fail because of this.
In summary, you need Customer Identity & Access Management that not only maps B2C use cases but is also dedicated to B2B use cases. Extensive group management is crucial in order to increase user comfort and also to reduce internal process costs through self-administration by customers. In addition, the integration of the identity providers (IdPs) of the customers offers great added value in the context of comfort and security for the users and is already a must-have criterion in some organizations.
Have already seen our last blog, “Customer Identity & Access Management and Customer Experience Become attractive qualities for Software as a Service (SaaS) Providers”!
